Pegasus Spyware - Science And Technology | UPSC Learning
Topics
0 topics • 0 completed
🔍
No topics match your search
Pegasus Spyware
Medium⏱️ 7 min read
science and technology
📖 Introduction
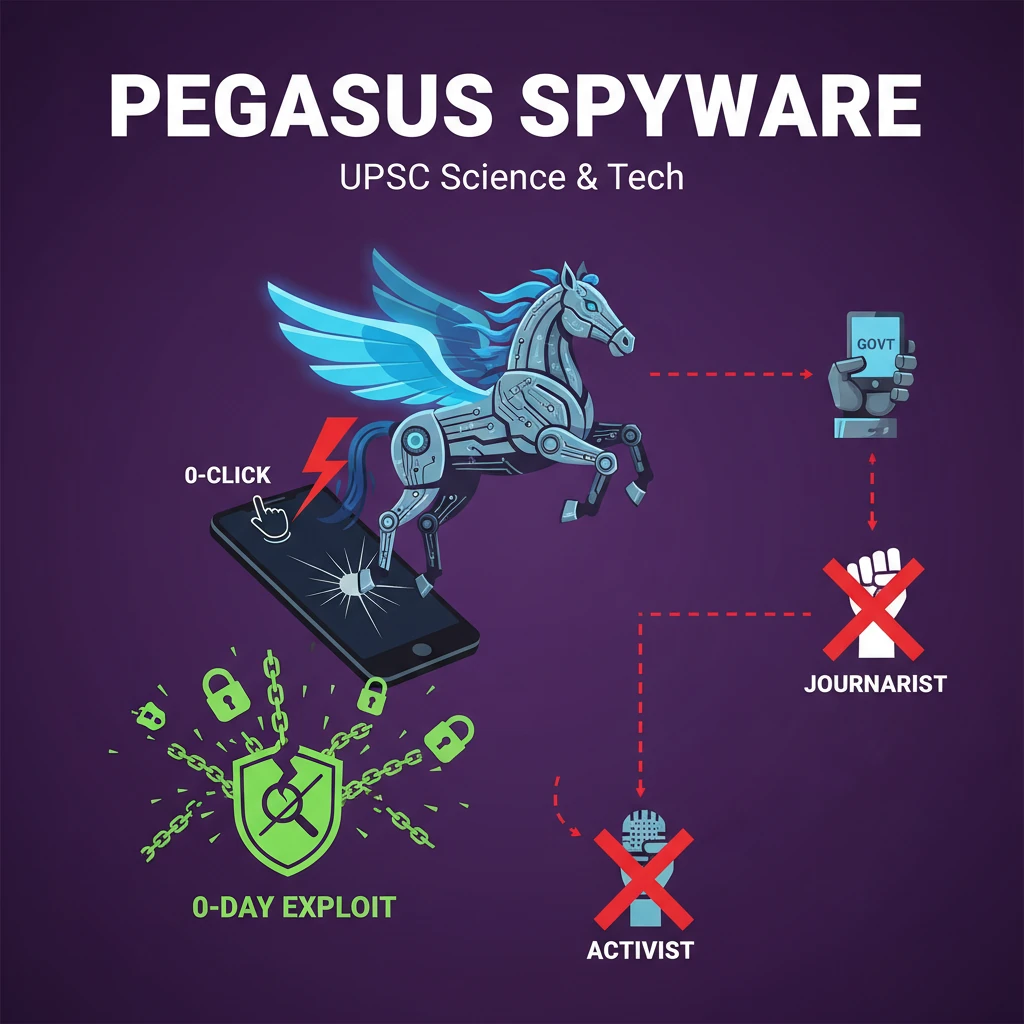
<h4>Introduction to Pegasus Spyware</h4><p>The <strong>Pegasus spyware</strong> has recently reignited critical debates surrounding <strong>privacy</strong> and <strong>national security</strong>. Its alleged use against prominent individuals globally, including in India, raises significant concerns about digital rights and government oversight.</p><div class='info-box'><p>Recent reports by <strong>Amnesty International</strong> highlighted the potential targeting of two prominent <strong>Indian journalists</strong> using Pegasus, prompting calls for investigations into possible government involvement.</p></div><h4>What is Pegasus Spyware?</h4><p><strong>Pegasus</strong> is a highly sophisticated and invasive <strong>mobile surveillance tool</strong>. It is designed to secretly infiltrate and monitor smartphones without the user's knowledge or consent.</p><div class='info-box'><p>This spyware is capable of collecting a vast array of <strong>data and information</strong> from various applications and sources on an infected device.</p></div><h4>Developer and Claims</h4><p>Pegasus was developed by the <strong>Israeli cyber-intelligence firm NSO Group</strong>. The company asserts that it sells this technology exclusively to <strong>government agencies</strong>.</p><p>NSO Group claims its product is intended solely for legitimate purposes, such as combating <strong>crime</strong> and <strong>terrorism</strong>. They also state they have mechanisms in place to prevent its misuse.</p><div class='key-point-box'><p>The <strong>NSO Group</strong> maintains that its spyware is not sold to target <strong>journalists, lawyers, or human rights defenders</strong> unless they are directly involved in terrorism or serious criminal activities.</p></div><h4>Operating Procedure: Zero-Click Exploits</h4><p>One of the most concerning aspects of Pegasus is its use of <strong>"zero-click" methods</strong> to infect devices. This means the spyware can be installed without any interaction or consent from the device owner.</p><p>Unlike conventional malicious software, Pegasus does not require the user to click on a suspicious link or open an infected attachment. It exploits vulnerabilities silently.</p><div class='info-box'><p>Pegasus can leverage flaws in popular applications like <strong>WhatsApp, iMessage, or FaceTime</strong>. It can initiate installation simply by sending a message or making a call, even if the user does not open or answer it.</p></div><h4>Zero-Day Vulnerabilities</h4><p>Pegasus is particularly potent because it can exploit <strong>zero-day vulnerabilities</strong>. These are undiscovered flaws or bugs within an operating system or software.</p><p>Since the manufacturer is unaware of these vulnerabilities, they have not yet developed a fix, making them extremely difficult to detect and prevent.</p><div class='key-point-box'><p>A <strong>zero-day vulnerability</strong> represents a critical security gap that software developers have not patched, allowing sophisticated attackers like Pegasus to bypass security measures effectively.</p></div><h4>Targets and Accusations</h4><p>Numerous investigations and reports have consistently revealed that Pegasus spyware has been used to surveil a wide range of individuals globally.</p><ul><li><strong>Journalists</strong> and <strong>human rights activists</strong></li><li><strong>Lawyers</strong> and <strong>opposition leaders</strong></li><li>Even <strong>heads of state</strong></li></ul><div class='info-box'><p>Countries accused of deploying Pegasus against critics and perceived enemies include <strong>Saudi Arabia, Mexico, India, Morocco, Hungary, Azerbaijan, and Rwanda</strong>, among others.</p></div><div class='exam-tip-box'><p>For <strong>UPSC Mains GS-II</strong>, understanding the ethical and legal implications of such surveillance tools is crucial, especially concerning <strong>fundamental rights</strong> and the role of the <strong>state</strong>.</p></div>
💡 Key Takeaways
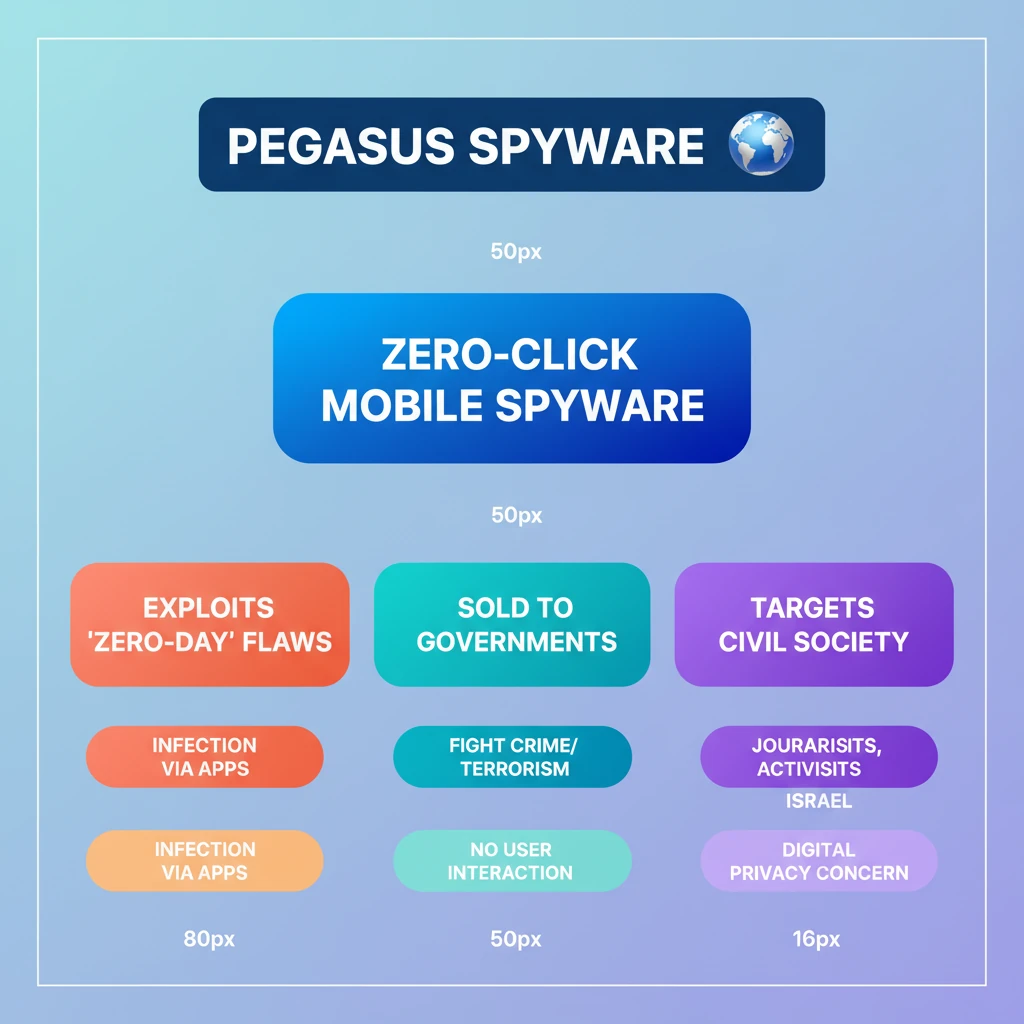
- •Pegasus is an advanced 'zero-click' mobile spyware developed by Israel's NSO Group.
- •It exploits 'zero-day vulnerabilities' in popular apps to infect devices without user interaction.
- •NSO Group claims it sells only to governments for fighting crime/terrorism, with safeguards against targeting journalists/activists.
- •Numerous global reports accuse governments of using Pegasus to spy on journalists, activists, and opposition figures.
- •The Pegasus controversy highlights critical issues of digital privacy, national security, government accountability, and judicial oversight.
- •It underscores the need for robust legal frameworks and strong cybersecurity measures to protect fundamental rights in the digital age.
🧠 Memory Techniques
95% Verified Content
📚 Reference Sources
•Amnesty International Reports on Pegasus Project
•Citizen Lab Research on NSO Group and Pegasus
•News reports from reputable international media (e.g., The Guardian, The Washington Post) on the Pegasus controversy